My last blog was about some flavours of fast secure roaming (FSR). Based on feedback from the community, especially from Nicolas Darchis (thanks), I´ve learned that its possible to enable fast secure roaming with both AKM-suite 1 (WPA) and AKM-suite 3 (FT over IEEE802.1X) on the same wlan (also possible with PSK). Cisco calls it Hybrid Mode
We can configure our Cisco WLC like this; enable Fast Transition and both 802.1X and FT 802.1X AKM-suite. The controller will warn you that some non-802.11r clients may not join this WLAN
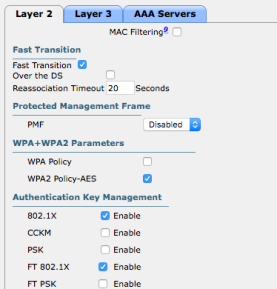
If we now look at the beacons or probe responses (from the AP) it will contain both AKM-suites in the RSN information element and the Mobility Domain information element. Like this.
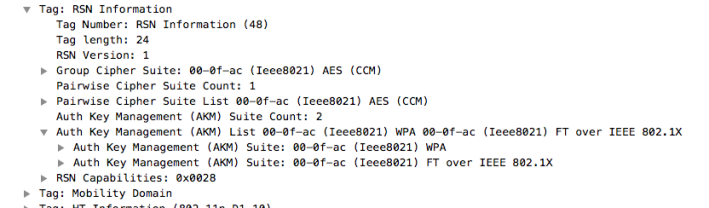
When a client wants to associate to this WLAN it will recognize those two AKM-suites and dependent of its own capabilities it will use one of these during association and re-association.
But why do we get the warning from the WLC during configuration and what about adaptive 802.11r. I have search on the web regarding this and found a Cisco support forum-case where Jerome Henry explains it, look here
A short brief (from that article)
It is basically 3 sort of clients (in regards to 802.11r)
- Those that support 802.11r (802.11r enabled)
- Those that not support 802.11r, but are not against it. They are 802.11r-compatible, but not 802.11r-enabled
- Those that are allergic to 802.11r. They do not support 802.11r, and refuse to associate to any WLAN where 802.11r is mentioned, even if other methods are also allowed on this WLAN
Testing in lab
I tested in my lab-network with WLC-configuration mentioned earlier and the same network/method as my last article. My test clients are a Samsung A5 (pretty new but simple Android-smartphone), an older Sony Z2 (smartphone on Android), iPAD2 (iOS ver 11.2.5) and a Lenovo Windows-client with Intel 6205 NIC.
Packets captures the initial association to original AP and captures on target AP when client roams. Cisco WLC-code is 8.3.122
The result
| Client | OS | Original AP | Target AP | Remark |
| Samsung A5 | Android | open authentication, open association, 802.1X/EAP-authentication, 4-way handshake | open authentication, re-association with PMKID in RSNIE, 4-way handshake | 802.11r compatible, but not enabled |
| iPAD2 | iOS | open authentication, ft-association, 802.1X/EAP-authentication, 4-way handshake | ft-authentication and ft-reassociaton | 802.11r enabled |
| Sony Z2 | Android | open authentication, ft-association, 802.1X/EAP-authentication, 4-way handshake | ft-authentication and ft-reassociaton | 802.11r enabled |
| Lenovo laptop with Intel 6205 NIC | Windows | open authentication/association, 802.1X/EAP-authentication, 4-way handshake | open authentication, re-association with PMKID in RSNIE, 4-way handshake | 802.11r compatible, but not enabled |
As we can se all client does fast secure roaming either with 802.11r( Fast BSS Transition) or Opportunistic Key Caching (OKC).
So what about category 3-clients that don´t bother to associate to this network. I haven´t find any overview over those clients. But best practice is to test your most important clients before implementation and if those weird client shows up they could enter a guest-WLAN.
What is the purpose of adaptive 802.11r
Cisco have a feature called adaptive 802.11r. Since my last blog I have wondered what the purpose of that, since enabling both WPA/OKC and FT on same WLAN works well. And again Jerome Henry in the same support forum case explains it best, look here
Adaptive 802.11r is a feature in a network where 802.11r is not enabled. With adaptive 802.11r turned on, iOS-devices will recognize 11r-feature and use FT. The other clients continues as before.
802.11r/FT for all clients (hybrid mode) would then be implemented after we had controlled our clients. We can look at adaptive 802.11r as a “zero-risk implementation” of 802.11r that helps IOS-devices to roam faster, without checking 802.11r-compabilities on all the other clients
MacBook (macOS)
I have not tested MacBook (MacOS) thorough since I use my MacBook for packet capture through Airtool. My80211.com have a great article on roaming behaviour on MacOS. But I did a short roaming test on my MacBook and I notice that it will not roam fast although RSSI from my original AP was -84dB and the target AP was 1m away from the client. It used several minutes before it roamed and that breaks with the -75dB rule I have learned earlier. So I have something to check
References

This is such a great blog. Thanks for taking the time to write it. Very thorough.
LikeLike
Thank you, sir
LikeLike
[…] links Gjermunds article about fast secure roaming, part 1 part 2 Eddie Forero, WiFiShark Fu, youtube video, Link Brian Long, The Anatomy of the 802 1X Association, […]
LikeLike