This is a blog article on 802.11ax uplink OFDMA (UL OFDMA) and the control frames that are involved.
According to the IEEE802.11ax draft 4 the UL OFDMA process look like this
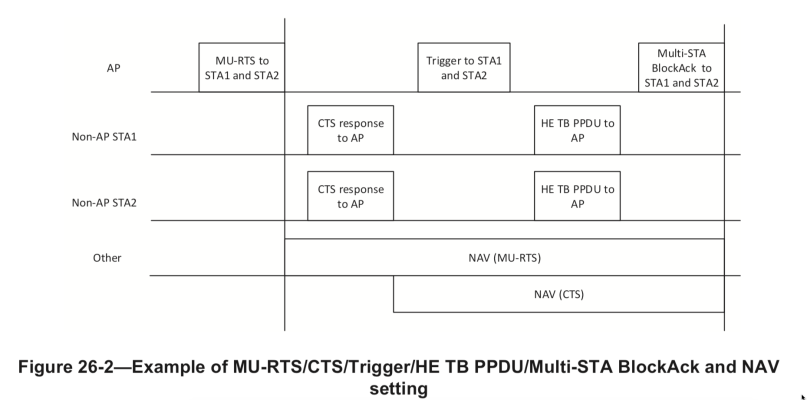
The MU-RTS and CTS are optionally and in some Cisco documentation, it says that the MU-RTS/CTS process is not needed. The MU-RTS/CTS process is described in another blog article. And as I say in that article, the MU-RTS/CTS process is not implemented by any vendors yet. And I also say it is better to use legacy RTS/CTS in a mixed environment, maybe.
My test lab is a Cisco Catalyst 9800CL (v16.12.1) wireless controller at Vmware Workstation, a Cisco Catalyst 9115 in FlexConnect mode, a Cisco 9115 in SnifferMode and two clients, a Samsung S10 and a Nano developer Kit with Intel AX200 NIC.
The attached pcap consists of three sessions (TXOP) of UL OFDMA, each consisting of three frames; Basic Trigger Frame, the Dataframe that is not captured and the Multi-STA ACK (0x0016)
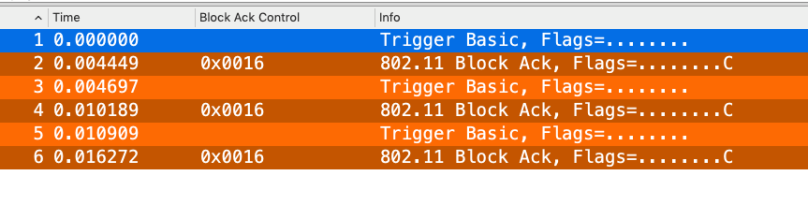
The uplink data that are sent in the HE TB PPDU format is not captured. I’m not sure whether it is a problem with Wireshark or the Cisco 9115 in Sniffer mode, but the information in the Basic Trigger frame and the Multi-STA ACK tells us enough information.
The Basic Trigger frame
Let’s start with the Basic Trigger frame. The Trigger frames are a new type of frames in the 802.11ax standard. The main purpose of the Trigger frames is to allocate resources and solicits one or more uplink HE TB PPDUs transmissions. The Basic Trigger frame is used to solicits the uplink data from one or more non-AP STAs
The frame format for a Trigger frame is like this
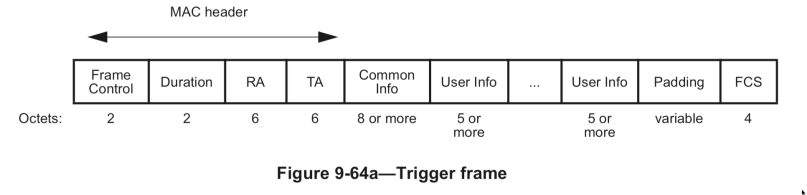
The MAC header
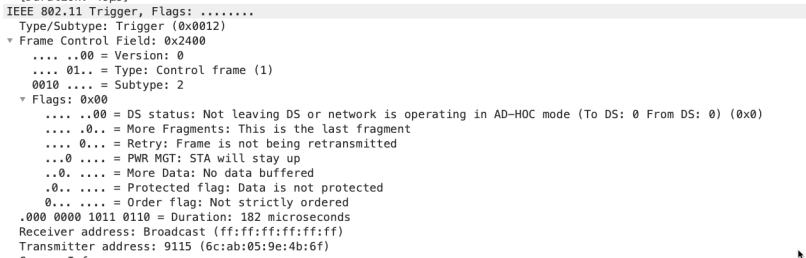
The most important thing:
– Control frame, type 1 and subtype 2
– Receiver address is the broadcast address
– Transmitter address is the AP that sends this frame
– Duration; distributing the NAV timer for this TXOP to all STAs in the BSS and on the channel
The Common Info field
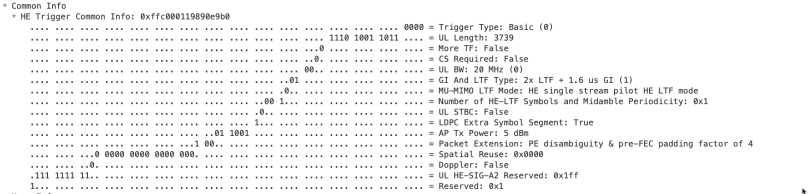
The field in the Common Info field is mostly information the non-AP STAs needs to build their frame for the uplink data. But these are something to look at:
– Basic Trigger frame, type 0
– UL Length: This value describes the Length of the uplink frame and shall be put into the Legacy Signal field and Lengths bit
– AP TX Power: The non-AP STA uses this value to calculate its TX-power
The User Info field
The Basic Trigger frame consists of one User Info field pr STAs that will send uplink data. In my lab, the two non-AP STAs (Samsung S10 and Nano Kit) has assigned STA-id (association id) 2 and 3
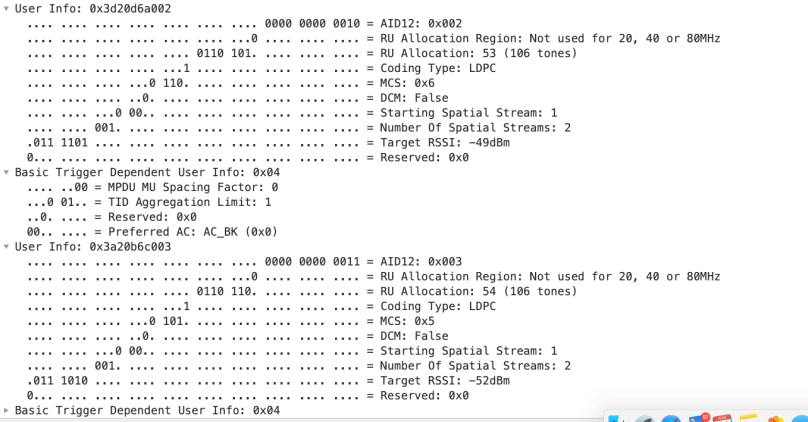
The most important subfield
– AID12 is the STA-id (association id) for the non-AP STA
– RU Allocation: describe which RU the STA is assigned to
– MCS; the MCS each non-AP STA should use. In this example, those two non-AP STAs will use different MCS. It is the AP that decide this value
– Target RSSI; This is the RSSI the AP want to receive each non-AP STAs uplink transmission at. Each non-AP STA calculate this value based on AP TX power from Common Info field and the RSSI it receives this Trigger frame at
RU Allocation
The RU Allocation subfield along with the UL BW subfield in the Common Info field identifies the size and the location of the RU. Table 9-31g in the IEEE802.11ax draft tells about all the possibilities
Four examples
– 9 times 26 tone RU at 20MHz, values 0-8
– 4 times 52 tone RU at 20MHz, values 37-40
– 2 times 106 tone RU at 20MHz, values 53-54
– 1 time 242 tone RU at 20MHz, value 61
Multi-STA BlockAck frame
The Multi-STA BlockAck frame is supported in uplink multi-user (UL MU). The BlockAck processes are diverse and I will only show the Multi-STA BlockAck frame
The MAC header is similar to other control frames
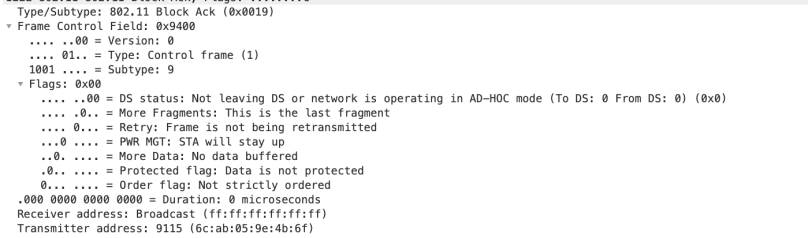
Since the Multi-STA BlockAck is sent til two or more non-AP STAs the receiver address (RA) is the broadcast address.
Next is the BA Control field
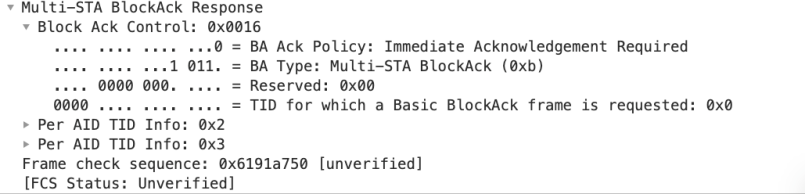 As we can see it is a Multi-STA BlockAck frame and it ACKs to AID (association ID) 2 and 3. The same AID as the AIDs in the basic Trigger frame
As we can see it is a Multi-STA BlockAck frame and it ACKs to AID (association ID) 2 and 3. The same AID as the AIDs in the basic Trigger frame
A closer look into one of the AIDs shows
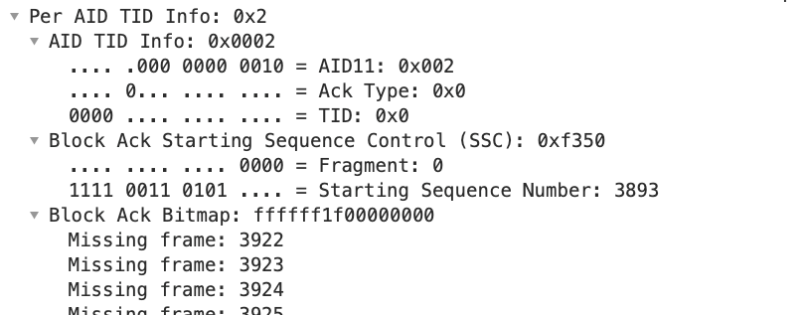
What this basically says is that it has received a lot of A-MSDUs (or A-MPDUs) where the sequence number on the first A-MSDU (A-MPDU) was 3893 and the last one was 3891. The parameter in Missing Frame is the next frame it expects to receive in the next TXOP
If we use the Starting Sequence Number as a column in Wireshark we will see an increasing number for both AIDs
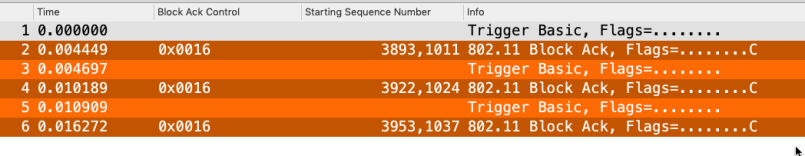
That’s all
If we want to see all the important information on one screen in Wireshark it could look like this
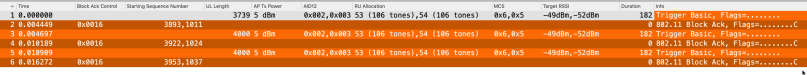
Attachment
Pcap (zip): UL OFDMA, Basic Trigger Frame and Multi-STA BlockAck.pcapng

Thanks for your excellent articles on 802.11ax. The UL OFDMA with trigger and multi-STA BA wherein you have attached a zip file as a trace does not display the trigger frames and multi-STA BA frames as mentioned. Could you please mention if there is any trick in seeing those frames
LikeLike
When I open the attached pcap it shows 6 frames, 3 sets of the Basic Trigger frame and the Multi-STA BA. Are you using Wireshark or another analyzer?. I use Wireshark
LikeLike
I’d also like to thank you for your excellent writeup of 11ax. I am having the same problem as Srikanth – they just look like ethernet frames. I am using wireshark.
Could you please tell me how to set up Wireshark to get, as you describe, “all the important info on one screen”.
I am using the Intel AX200 STA as a sniffer – you have to tell which AID to look for, but it does work.
LikeLike
I have two articles and a video where I explain how to capture Multi-User frames during DL OFDMA and Trigger-based frames during UL OFDMA.
Check these and try to do it likewise.
The article you have send the comment from is from August and back then I didn’t know how we captured MU and TB frames
https://gjermundraaen.com/2019/11/16/wireless-capturing-of-multi-user-ofdma-frames/
https://gjermundraaen.com/2019/11/24/wireless-capturing-of-ul-ofdma/
https://gjermundraaen.com/2020/01/06/vlog-how-to-capture-802-11ax-ofdma-traffic-with-jetson-nano/
Thank you for the feedback
LikeLike
Thank you for your guidance.
About the attached a zip file. It incould fake ethernet header.
It cannot display the trigger frames. The frame protocol is UDP.
LikeLike
If you are using Wireshark, and I have used an AP in sniffer mode the frames are sent to Wireshark as UDP packets.
Click on one of the frames, right click and select «Decode as»
Find «Peekremote».
Please send feedback
LikeLike
Thanks for the blogs on 802.11ax.
I am facing the same issue on the pcap. i checked in the latest version of wireshark in linux mint and in windows 10. In both the cases i am seeing only UDP packets and not the packets as shown in your blog,
LikeLike
[…] AP in a frame called the Basic Trigger frame. This is usually a control type of frame. My article, UL OFDMA, basic Trigger Frame and Multi-STA BlockAck, explains this process.Another of my previous articles, UL OFDMA- Make RF Collisions Work, has a […]
LikeLike
[…] UL OFDMA Basic Trigger Frame and Multi-STA-BlockACK From Gjermund Raeen: https://gjermundraaen.com/2019/08/26/ul-ofdma-basic-trigger-frame-and-multi-sta-blockack/ […]
LikeLike