How to capture frames in Wireshark on a network with WPA2 Enterprise and AP in FlexConnect using MacBook
My lab network looks like this

Remarks
– SW2 with AP, trunk against AP with vlan 1716 (ap management) and vlan 2000 (flex WLAN), 1716 as native vlan
– SW2, all vlans enabled on all trunkports
– Router, two LAN-subinterfaces and internal dhcp-server for both subinterfaces, nat against internet
– Radius-server (authentication server). Ubuntu-client. Free Radius server, configured for EAP-PEAP and EAP-MSCHAPv2
– WLC (authenticator): Wlan with wpa2-aes and 802.1X, access point in flexconnect with native vlan to 1716 and the flex WLAN mapped to vlan 2000
– Android smartphone (supplicant). Mac-address on wifi-nic: 5c;51;81;22;4d;a1
Traffic flow

The traffic flow in this network is like this
- Phase 1: Establish 802.11 data link: probe request/response, authentication and association between the client and the AP
- Phase 2: Starts with the authenticator (WLC) sends request identity to the supplicant (client) and the supplicant respond. The virtual uncontrolled port on the authenticator opens and allow EAP-traffic through (the red line). An important part of this process is the traffic flow between the authenticator and authentication server (the blue line)
- Part 1 is the authentication of the client. It ends with an Access-Accept from the authentication server to the authenticator and EAP-Success from the authenticator to the supplicant
- Part 2 is creation of crypto keys (4-way handshake). When the last message (message 4 of 4) is acknowledged the virtual controlled port authenticator opens and traffic from the client will flow directly to the router in the flex-vlan
- Phase 3: The supplicant (client) is authenticated and crypto keys are generated. The client is now able to start the dhcp-process and all traffic flow in the flexconnect-vlan directly to the router (the green line)
Capturing frames
I want to capture these frames
– between the wireless client (client) and the access point (AP), in the air
– between the AP and the controller (WLC)
– between the WLC and the radius-server
– between the client and the router when the client are authenticated and crypto keys are generated (ordinary traffic)
To manage that we have to capture into the air and at SW1 port g1/0/14 and g1/0/28
I am using Cisco equipment so it´s possible to use SPAN-ports (port mirroring). Some switches will not distribute vlan-tags natively on SPAN-port so I had to configure it. The commands on the SW1
– monitor session 1 source interface g1/0/14 , g1/0/28
– monitor session 1 destination interface g1/0/3 encapsulation replicate
To capture the wireless frames I´am using a MacBook Pro and Airtool from Adrian Granados.
The packet analyser is Wireshark
Start capturing
MacBook connected to SW1, g1/0/3, via ethernetport
The client wifi-nic either deactivated or connected to another SSID. It´s also best to “forget” the actual SSID on the client so that we are sure the client have to go through the hole 802.1X EAP-process
– Start the capture in Wireshark on your ethernet-port
– Start wireless capture in Airtool at the channel your SSID are transmitting
– Activate your client on the flex connect SSID and log on with your username and password
– Wait until the wireless client is connected
– Stop capture in Wireshark and Airtool
Merging capture files in Wireshark
Airtool will automatically save the capture on your desktop. Save your wired capture from Wireshark to the desktop.
Clean your window in Wireshark with File/Close.
Drag the two captures from Desktop into Wireshark. Now the two captures will merge together and since they both uses the same clock from the MacBook all the frames will be stacked in the correct order
Time to filter important frames
With our setup the capture will consist several frames from the same transmission, from the capture points. The capture can consist of several 1000s frames depending of which type of traffic there is on the network, especially if we had captured from a production network. We will use display-filter in Wireshark to filter out those frames of interest.
Filter wireless frames
It is one address that are important to find, the Mac-adress of the wireless client. It can be found in different ways. Either from Utilities on the client, from an app like Net Analyzer on the wireless client or from one of the captured frames. In this example we will find it from one of the frames
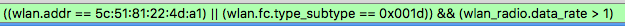
- Find one of the wireless frames in your capture. The easiest way is to filter on EAP. Make sure that you find a wireless frame. If you have columns with Data Rate or Signal Strength those should show a value. Go into IEEE 802.11 packet details in Wireshark and find your wireless clients Mac-address, either as receiver address (RA), transmitter address (TA) or destination address (DA). Right click and prepare or apply as filter. To make sure to show frames in both direction change either “wlan.ra”, “wlan.ta” to “wlan.da” to “wlan.addr” like this

- If you apply that as a filter the capture will show all management, control and dataframes to and from your wireless client except the ACK-controlframe from your wireless client towards the access point. This frame, which acknowledge unicast frame from the access point to your wireless client, only have one address which is the receiver-address of the AP. It´s difficult to filter out the ACK specially from the your client to the AP, so we filter out all ACK-frames with this filter

- If we filter on those from 1 and 2 the capture will still show frames from the wired side. To make sure to only see wireless frame we have to find a filters that only show wireless frames. One alternative is the Data rate parameter from the 802.11 radio information section. Select this and change it to show 1 Mb/s or higher (all possible data rate

- Bring it all together and it will show all wireless frames between the wireless client and the AP

or like this
Filter Frames between the AP and the Controller
Almost all the frames in the phase where the wireless client are contained into the virtual uncontrolled port of 802.1X-EAP process that goes between the AP and the controller. These frames are tunneled inside the Capwap-tunnel. To filter out these we could use the filter from above with some modification. Change the filter to show frames from the wired side, i.e. frames not containing “wlan_radio.data.rate”. Change “and” to “and not” Like this.  .
.
This view shows all traffic on the wired capture points between the client and the WLC, inside the capwap-tunnel.
If we now make a filter that combine all together we could use this 
Filter Radius-frames between the controller and the Radius server
This one is quite easy. It´s just to filter on “Radius”

Filter for all the frames when the authenticator has the virtual uncontrolled port open
With this filter we are able to see all frames from the client joins the SSID and to the client are authenticated and crypto key are generated
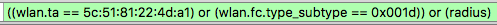
Filter on ethernet-frames
During authentication, association, EAP-authentication and 4-way handshake all traffic to and from the wireless client goes inside the control-tunnel between the AP and the controller. When the client is authenticated and all crypto keys are generated (4-way handshake) the client will be moved from the virtual uncontrolled to the virtual controlled port of 802.1X-process and traffic will moved over to the vlan for the flex connect-SSID. Since the SSID on the AP is in flex connect, all traffic will flow in the flex connect vlan between the AP and the gateway-router, and not through the controller.
Those packets can be filtered by using the clients mac-address, but now we have to filter them as ethernet addresses. The best way to find those packet is to find the IP address for the client after the dhcp process. Either by looking at the dhcp-server, at the wireless client or filter in Wireshark with “bootp”. Or just search for other frames with the assigned IP address. When one of these frames are found, look into the ethernet packet detail and find the mac-address for the client. Here we also have to change the filter to show frames in both direction. The filter should look like this

The final filter in Wireshark
Above are the filters for each type of frames we are looking for (frames of interest) during the WPA2 Enterprise authentication process. Bringing it all together we will have a Wireshark-filter like this

or

What we have
With the last filter we will see at lot of frames. When the client is inside 802.1X-EAP virtual uncontrolled port the same transmission is seen in three different frames.
– between the client and the AP, wireless frame
– on the trunk between SW1 and SW2
– on the trunk between SW1 and the controller
– and vice versa
When the wireless client are moved over to the virtual controlled port in 802.1X-EAP process the same transmission will be seen twice
– between the client and the AP, wireless frame
– on the trunk between SW1 and SW2, towards the router
– and vice versa
Note: since we have two capture files that are merged together it could happen that the wireless frames and the wired frames have changed order.
What is it possible to find
With those filters it should be possible to find all frames of interest during
– probe request/probe response
– authentication/association
– 802.1X-EAP authentication
– 4 way handshake
– DHCP
– ARP
– normal traffic to and from the Internet.
How to do it in Windows
I have used MacBook Pro and Adrian Granados Airtool to capture wireless frames. To do the same in Windows it is more difficult since Windows can´t natively capture wireless frames in promiscuous mode. But amyengineer.com and sniffwifi.com have blogarticles on howto capture wireless frames with Acrylic wifi

Do not think Acrylic will work on the wireless side for all frames. Aas far as I know Acrylic have difficulties tracing multiple stream packets (Unicast data), with the current supported list of dongles listed on their site. May though have to try again to see if something changed. Acrylic uses NDIS drivers where currently some development is ongoing with open source drivers and also some work by Metageek.
Using Omnipeek instead, will just work great. And the above process of writing filters etc much easier.
LikeLike
I didn’t´t worked well for me with Acrylic, but I know Amy was satisfied at least for learning experience. I have used a D-Link DWA-182 version C usb-dongle for frame capture with CommView for Wifi, but I can’t capture all types of frames simultaneous. Either I have to capture managements frame or control/data-frames. At MAC wireless frame capture is more easy, together with freeware Wireshark.
Omnipeek is quite expensive
LikeLike
Yes but dongles very cheap. And can run on a cheaper Windows PC and have many channels recorded simultaneous. Record is 14 by Jerry Olla. Omnipeek has a a very good report tool and statistics analysis built in something that normally needs add ons to Wireshark or export to Excel.
LikeLike
[…] the best way to remember the theory is to see whats actually happens with a packet capture. My last blog was on how to do packet capture and using display-filter in […]
LikeLike